



Upload Rulebook
Upload ITGC and ITAC controls rule book




Upload ITGC and ITAC controls rule book
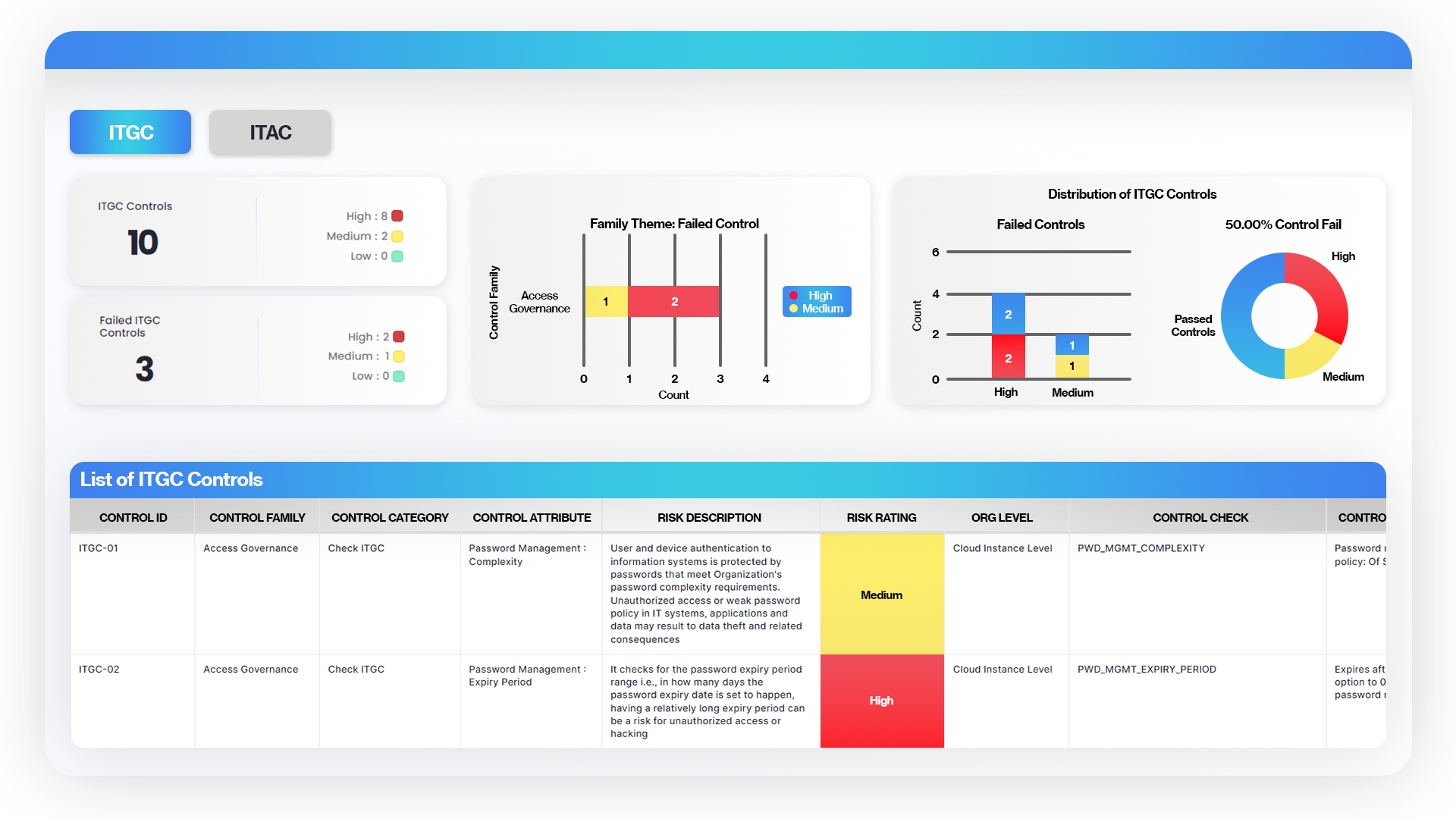
Interactive Dashboard gets populated







One-click reporting utilizes state-of-the-art in-house generative AI, revolutionizing efficiency and insight generation in the tool.
ITGC play a vital part from creating a new user’s creation of accounts to password security and software security and modifications. ITAC is a security control that helps in blocking suspicious applications from running something malicious which can cause risks to the company. ITAC lets authorities comprehend if all the data imputed in the software are correct and safe.
Tools regarding data automation utilize robotic process automation (RPA) which results in an intense effect on the IT control areas. Automation helps in managing IT, tracking, and remediating the IT general controls effectively for accurate and better results.
✔ Automation of IT controls helps in saving a huge amount of time.
✔ IT control automation is fully secure and accurate giving precise results.
✔ Automated monitoring is available 24×7 making sure that every fragment of data is secure.
✔ Helps in creating new users and limiting access to only privileged users for better data security.
✔ iRM prioritizes providing extra and better security to important and most critical data from getting violated.
✔ iRM collaborates with different ERPs like Oracle, SAP, Workday, and many more for better accuracy and financial support with a large number of preset rules.
✔ Creation of Super users which means only they can create or delete users and assign roles.
✔ Due to continuous monitoring, Super users get notified when there is a potential risk or suspicious activities and
instantly take action like 2FA and password changing or access review.
ITGC (Information Technology General Controls) plays a crucial role in ensuring the security and integrity of IT systems. It encompasses processes from creating new user accounts to maintaining password security and overseeing software modifications. ITGC ensures that these processes are conducted securely and efficiently.
Automating IT controls offers several advantages, including substantial time savings, enhanced security and accuracy in results, continuous monitoring for data security, and the ability to create and manage user access more effectively.
iRM collaborates with various Enterprise Resource Planning (ERP) systems like Oracle, SAP, and Workday. This integration allows for better accuracy in data management and financial transactions, supported by a large set of predefined rules.
ITAC (Information Technology Access Control) is a security measure that blocks suspicious applications from executing potentially harmful actions. It helps authorities verify the correctness and safety of data inputted into software, thereby mitigating risks to the company.
iRM (Integrated Risk Management) focuses on providing enhanced security to safeguard critical data from breaches. It employs advanced security measures to protect sensitive information from unauthorized access or violations.
Continuous monitoring in iRM enables Super users to be promptly alerted of potential risks or suspicious activities. This immediate notification allows for quick actions, such as implementing two-factor authentication (2FA), changing passwords, or reviewing access permissions, thereby enhancing overall security.